A fundamental concept of modern security, encryption, serves as the cornerstone to safeguard data storage, digital communications, streaming, online transactions and much more. Derived from the roots of cryptography, encryption transforms a plain, readable information into an unreadable or unintelligible form using mathematical algorithms and secret keys. The same data is decrypted using a decryption key at the client/user’s end. The overall purpose of encryption is to make sensitive data confidential and secure, restricting unauthorized access, sharing or copying. To simplify the content protection process for video creators and distributors, CENC, or Common Encryption Scheme ensures interoperability between various DRM systems. CENC common encryption methods and algorithms also plays an important role in secure and seamless digital media delivery to a range of devices and systems.
Table Of Content:
Furthermore, encryption safeguards sensitive information stored on servers, smartphones, browsers, and personal computers from hacking and piracy. As the presence of the online world is rapidly progressing, the importance of encryption in our professional and personal lives has grown more critical, playing a key role in fighting piracy and securing our digital ecosystem.
Explore More ✅
VdoCipher ensures Secure Video Hosting for OTT Platforms
VdoCipher helps over 3000+ customers from over 120+ countries to host their OTT videos securely, helping them to boost their video revenues.
How Does Encryption Work?
Here’s the basic outline of the encryption technology in simple words:
Key Generation – Before encryption or decryption happens, a secret key is generated. The key can be single for symmetric encryption or a pair of two keys for asymmetric encryption. The encryption strength depends on the algorithm used and key size.
Encryption Algorithm – Using an encryption algorithm, the plaintext data is processed and converted into ciphertext. It applies a combination of mathematical operations and transformations. There are several encryption algorithms including DES (Data Encryption Standard) and AES (Advanced Encryption Standard).
Data Encryption – The sender inputs the secret key and plaintext data into the encryption algorithm which further transforms the plaintext into ciphertext. It is then ready to be transmitted without any unauthorized user having access to it.
Data Transmission – Once the encrypted data is transmitted, it remains unreadable to anyone without the decryption key.
Decryption – Upon receiving, the authorized user uses a decryption key to decrypt the ciphertext into the plaintext using an encryption algorithm.
Data Integrity Verification – During storage or transmission, to ensure the data is not hampered, additional mechanisms are often employed. For example, message authentication codes, hashing, or digital signatures.
Types of Encryption
Symmetrical Encryption
In symmetrical encryption, a single shared key is used to both encrypt and decrypt the content files. Both the sender and receiver must have the same key to securely exchange the information. It is commonly used for bulk data encryption and secure communications in a closed ecosystem.
Asymmetrical Encryption
Asymmetrical encryption is also known as public key cryptography. It uses a pair of related keys, one for encryption (public key) and the other for decryption (private key). To encrypt data with that public key, the only way to decrypt is via the corresponding private key you have access to.
Furthermore, you can also reverse the key flow. One can encrypt the information through a private key, and only people with the public key can decrypt it. This is the mechanism that we use for doing a digital signature, for example.
Symmetric vs Asymmetric Encryption | Tabular Comparison
| Attribute | Symmetric Encryption | Asymmetric Encryption |
| Key type | Single shared secret key | Two related keys: public key and private key |
| Key usage | Same key for encryption and decryption | Public key for encryption, private key for decryption |
| Speed | Faster, as it uses simpler operations | Slower, due to more complex calculations |
| Key distribution | More challenging, as the secret key must be shared securely | Easier, as only the public key needs to be shared and can be done so freely |
| Use case | Bulk data encryption, secure communication within closed systems | Secure communication over open networks, digital signatures, key exchange |
| Examples of algorithms | AES (Advanced Encryption Standard), DES (Data Encryption Standard), Blowfish | RSA, ElGamal, ECC (Elliptic Curve Cryptography) |
| Key management complexity | Higher, as the number of keys increases exponentially with the number of users | Lower, as each user only needs one public-private key pair |
| Security | Depends on the key size and the algorithm used | Generally considered more secure due to separate keys for encryption and decryption |
Importance of Encryption for the Video Industry
For the video industry, video encryption is very important. Here are some reasons why:
- To protect Intellectual Property – video content such as movies, and shows take a lot of time and effort. Encryption provides means to protect their intellectual property from unauthorized access, copying, and sharing.
- To secure content distribution – to enforce licensing agreements and restrict access to their premium content, content creators and distributors use encryption. Platforms like Netflix use DRM (Digital Rights Management) to encrypt their video content.
- Maintain user privacy – Today video platforms store a lot of information and data such as preferences, payment options, and viewing habits. To maintain trust and user privacy, the data is secured via encryption.
- To meet compliance requirements – Many regions and industries require the mandatory protection of sensitive data. In the field of videos, encryption technologies like video DRM help in complying with these regulations.
What is CENC Common Encryption Methods & Algorithms?
The most popular and used video streaming protocols are MPEG-DASH and HLS. On one side, HLS uses (ts) container format for its videos while MPEG-DASH uses mp5 format. The first problem is, if a content provider uses both these protocols, then they need to store video files in both formats. Secondly, it’s a total waste of storage space.
To address the first issue, CMAF (Common Media Application Format) specification was developed. Here, the videos are stored in fragmented mp4 container format (fmp4). Now, instead of two separate video formats, you have to store the video in fmp4 format, using common file sets for both protocols.
What if different DRM technologies use different encryption standards?
MPEG developed the Common Encryption Scheme (CENC) that standardized the method of media content specified by ISO/IEC 23001-7.
Explore More ✅
Protect Your VOD & OTT Platform With VdoCipher Multi-DRM Support
Vdocipher helps several VOD Platform to host their videos securely, helping them to boost their video revenues.
CENC defines a common set of encryption and key mapping methods that are compatible with different DRM systems. CENC is based on the MPEG Common Encryption (MPEG-CENC) standard which is supported by various platforms, including web browsers, mobile devices, and smart TVs. Also, CENC is used in various multimedia content distribution platforms such as Netflix, Amazon Prime, Hulu, and YouTube.
This allows content providers to encrypt their media once and use multiple DRM systems for content protection simultaneously. This is particularly useful for adaptive streaming formats like MPEG-DASH and HLS, where the media is delivered in smaller segments to ensure smooth playback across various devices and network conditions.
| Streaming Format | Container Format | Compatibility with CENC |
| MPEG-DASH | fMP4 | Yes |
| HLS | fMP4 | Yes |
| HLS | MPEG-2 TS | No |
CENC Encryption Algorithms
CENC common encryption methods and algorithms does not have a specific encryption algorithm, instead supports multiple encryption algorithms. Some of the common encryption algorithms CENC supports are:
AES-CTR (Advanced Encryption Standard – Counter Mode)
AES-CBC (Advanced Encryption Standard – Cipher Block Chaining)
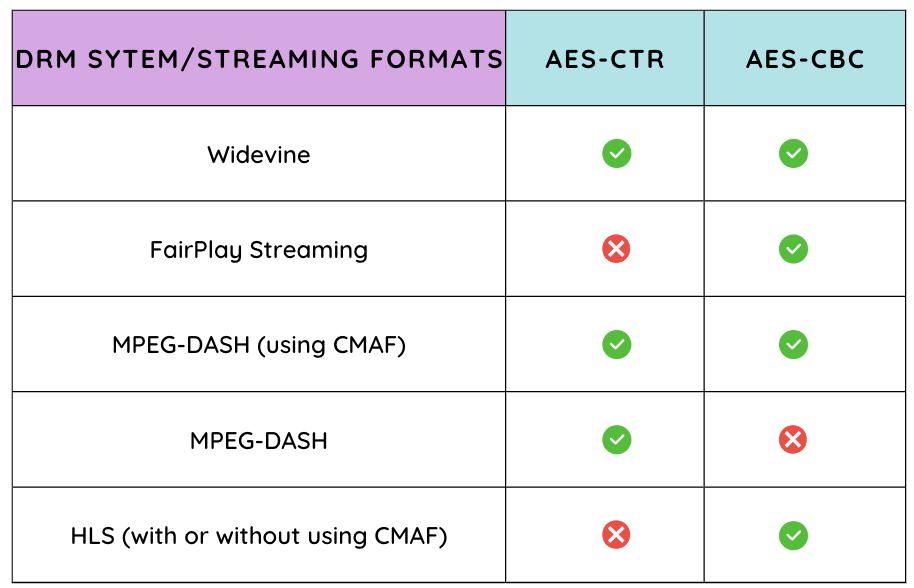
These two modes do the encryption handling differently and are not compatible with one another.
Primarily, there are two DRM technologies, Google Widevine, and Apple FairPlay. Different technologies have varying levels of support for each encryption standard. The points of difference between the two are how they handle the plaintext blocks and initialization vector, IV (first ciphertext block)
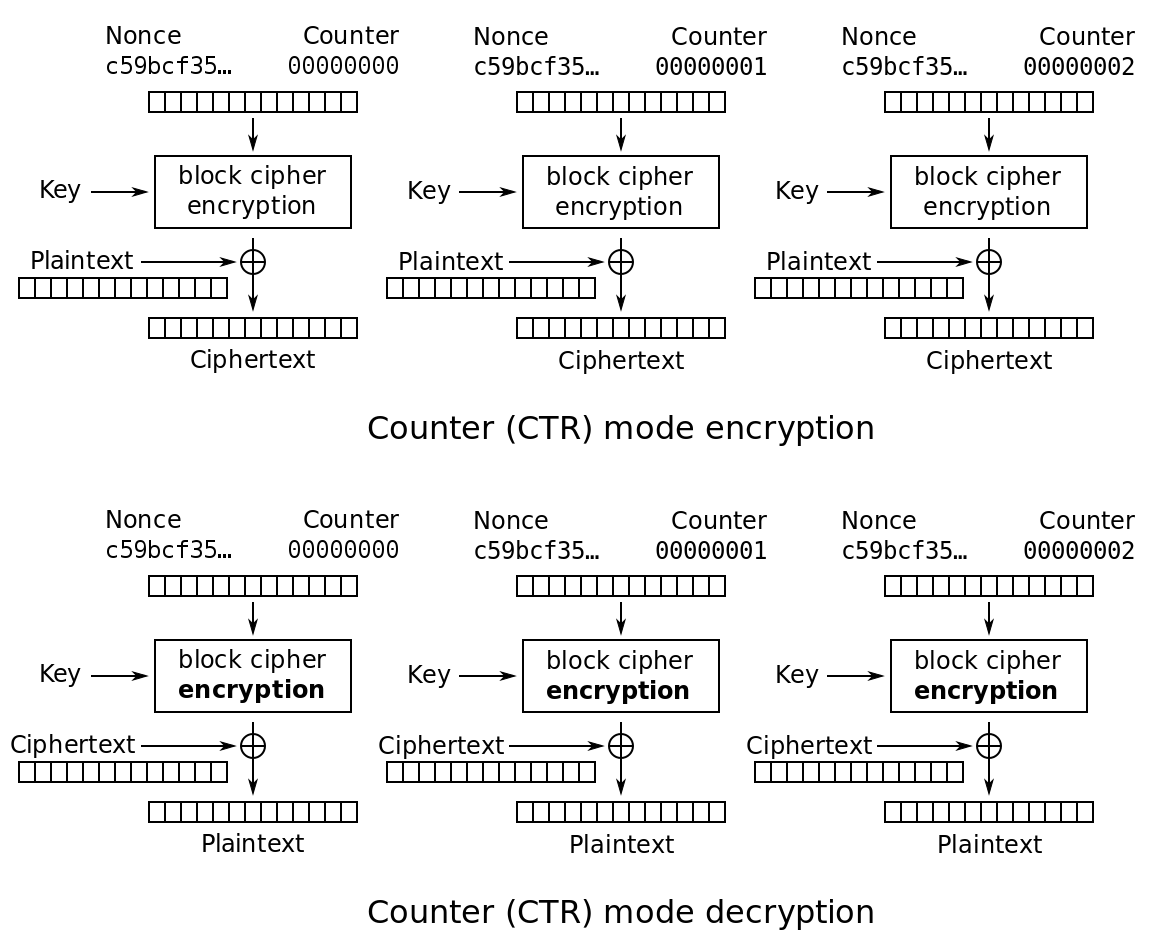
CTR (Counter Mode)
source: wikipedia
- CTR converts a block cipher into a stream cipher using encrypting successive values of a counter.
- It generates a unique input which is a combination of a nonce and a counter for each data block.
- The counter is incremented for each subsequent data block to ensure uniqueness.
- For each subsequent data block, the counter increments.
- The block cipher then encrypts the counter value via the secret key to produce a keystream block.
- The keystream block is XORed with the plaintext block to generate the ciphertext block.
- CTR enables parallel encryption and decryption so that each block can be processed independently of others.
- It doesn’t require padding for the plaintext data, making it more efficient for media content.
- For random IV/nonce – combining with a counter through any invertible operation like XOR, concatenation to produce a unique encryption counter block.
- For non-random nonce (example packet counter) – nonce and counter are concatenated.
- Just adding or XORing the nonce and counter into a single value may break the security under plaintext attacks. The attacker may be capable of altering the entire IV-counter pair.
- Once accessed, the XOR of the plaintext with the ciphertext will have a value that when XORed with the ciphertext of another block having the same IV-counter pair, would decrypt the block.
| CTR (Counter) | |
| Encryption parallelizable | Yes |
| Decryption parallelizable | Yes |
| Random read access | Yes |
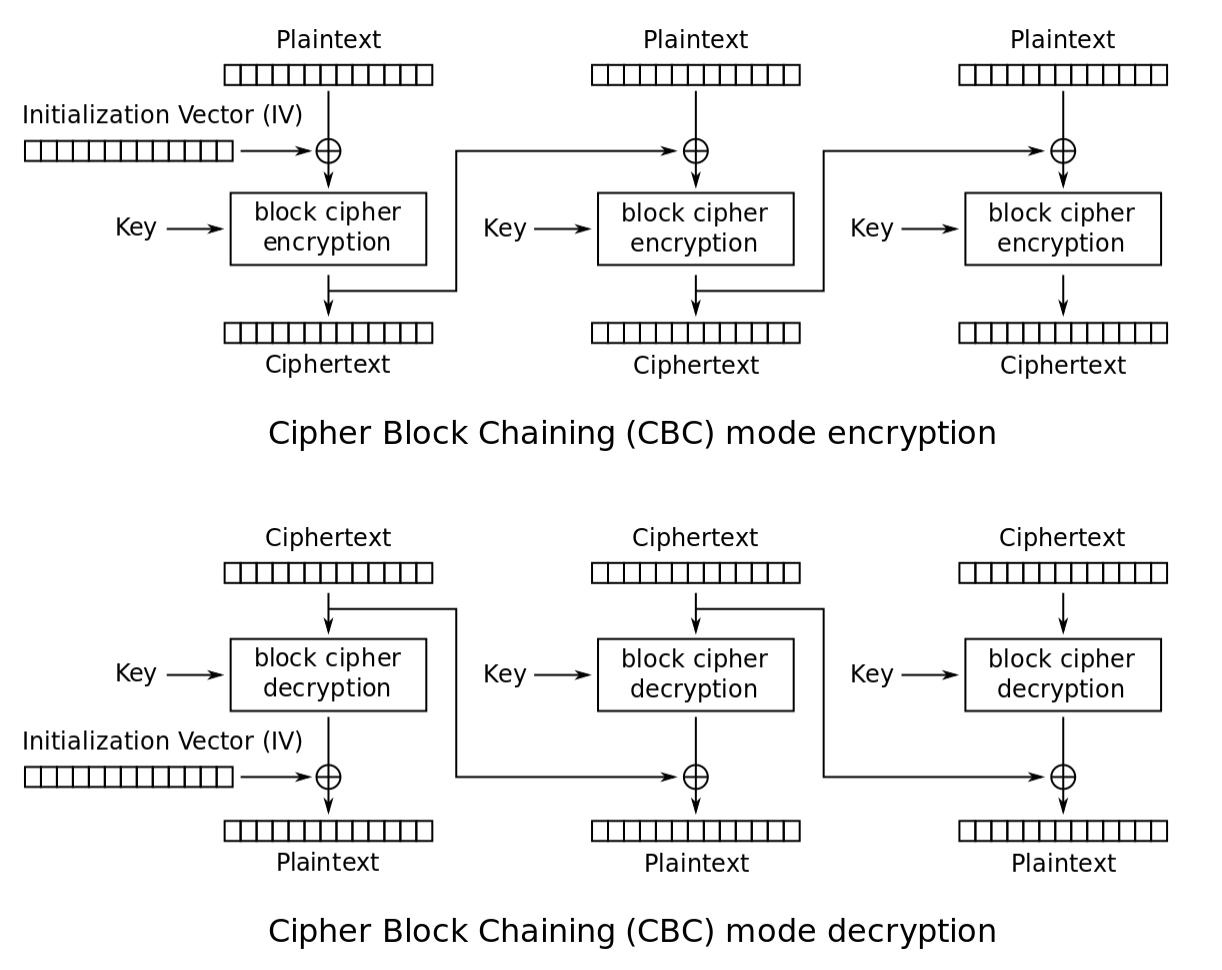
CBC (Cipher Block Chaining)
source: wikipedia
- CBC encrypts plaintext in fixed-size blocks (e.g., 128 bits for AES).
- An initialization vector (IV) ensures an unique ciphertext for the same plaintext with the same key.
- Before encryption, the IV is XORed with the first plaintext block with the block cipher and the secret key, producing the first ciphertext block.
- The previous ciphertext block is XORed with the current plaintext block before encryption for each subsequent block, creating a dependencies chain.
- Decryption requires processing the ciphertext blocks in reverse order due to the chaining mechanism.
- CBC lacks parallelism, as each block’s encryption or decryption depends on the previous block’s ciphertext.
It requires padding for the plaintext data, which can lead to inefficiencies.
| CBC (Cipher block Chaining) | |
| Encryption parallelizable | No |
| Decryption parallelizable | Yes |
| Random read access | Yes |
- One major disadvantage of CBC is that it requires sequential encryption, meaning you cannot encrypt multiple blocks simultaneously (no parallelization). This can make the process slower compared to other encryption modes.
- Another drawback is that the message must have a length that is a multiple of the block cipher’s size. This often requires adding padding (extra bits) to the message to meet the required size.
- “Ciphertext stealing” is a technique used to address the padding issue mentioned above, allowing encryption without padding. In CBC, if there is a one-bit change in the plaintext or the initialization vector (IV), all the following ciphertext blocks are affected. This property can be both an advantage and a disadvantage, as it increases security but also makes error propagation more likely.
CENC Common Encryption Methods & Algorithms Support
Some major browsers, devices, and platforms supporting CENC are:
Streaming Protocols:
MPEG-DASH (Dynamic Adaptive Streaming over HTTP)
HLS (HTTP Live Streaming)
DRM Systems:
Google Widevine
Apple FairPlay Streaming
Microsoft PlayReady
Devices and Platforms:
Many smart TVs
iOS and Android devices
Web browsers such as Google Chrome and Safari
CENC Implementation
Common Encryption Scheme (CENC) is pretty straightforward for developers having knowledge of media streaming, encryption process, and most importantly DRM systems. Based on the project’s complexity and the developer’s expertise, the CENC implementation varies.
Some factors to consider while implementing CENC include
DRM Systems – CENC works with multiple DRM systems, such as Google Widevine and Apple FairPlay Streaming. The developer must understand the intricacies of each DRM system being used and ensure proper integration with CENC.
Streaming Protocols – Implementing CENC requires knowledge of the streaming protocols being used, such as MPEG-DASH or HLS streaming. The developer must understand how CENC is integrated with these protocols to provide secure content delivery.
Encryption Algorithms – CENC supports multiple encryption algorithms, like AES-CTR and AES-CBC. The developer needs to be familiar with these encryption algorithms and their proper implementation within the CENC framework.
Key Management – Proper key management is essential for secure content protection. The developer must ensure that encryption keys are securely generated, stored, and distributed and that the right keys are used for the appropriate DRM systems.
Compatibility – Ensuring compatibility across various devices and platforms can be a challenge, as each may have unique requirements and limitations. Developers must thoroughly test their CENC implementation to ensure seamless content delivery and playback.
VdoCipher Secure Multi-DRM Solution
VdoCipher, a secure video hosting platform offers the highest available video security to protect your premium content from piracy and unauthorized access or sharing. Being a direct partner with Google for Widevine DRM, VdoCipher offers Multi-DRM solutions with Apple FairPlay and Google Widevine DRM support. Videos streamed via VdoCipher cannot be illegally downloaded or hacked using any internet plugin or software.
More than 3000 customers across 120+ countries rely on VdoCipher to securely host and stream their premium content. The various features offered by VdoCipher are:
- Multi-DRM Encryption
- Dynamic Watermarking
- Custom Video Player for Android, Desktop, and iOS
- Secure offline downloads in Android
- Screen Capture Prevention
- Ready to use Plugins for WordPress & Moodle
- Easy Embed Options
- Domain/IP Restrictions
- Adaptive Bitrate Streaming
- Video Analytics
FAQs
What are the advantages of CENC?
Interoperability between DRM systems, easier content distribution, reduced costs in managing multiple DRMs, and simplified workflow.
Is CENC common encryption methods and algorithms secure for my videos?
CENC security depends on the DRM systems it supports and the underlying encryption algorithms. When implemented properly, CENC can highly secure digital content.
Name some most common encryption methods
Advanced Encryption Standard (AES), Data Encryption Standard (DES), RC4, Triple Data Encryption Standard (3DES), and RSA.
Supercharge Your Business with Videos
At VdoCipher we maintain the strongest content protection for videos. We also deliver the best viewer experience with brand friendly customisations. We'd love to hear from you, and help boost your video streaming business.


Jyoti began her career as a software engineer in HCL with UNHCR as a client. She started evolving her technical and documentation writing skills to become a full-time Content Marketer at VdoCipher.